Network Security & Survivability
|
SOS and WebSOS: Secure Overlay Services |
| SOS
is a network overlay mechanism designed to counter
the threats posed by Distributed Denial of Service
attacks (DDoS).
WebSOS, is an adaptation of SOS for the Web
environment that guarantees
access to a web server that is targeted by a distributed
denial of service (DDoS) attack.
Our approach exploits two key characteristics
of the web environment: its design around a human-centric
interface, and the extensibility inherent in many
browsers through downloadable “applets.”
We guarantee access to a web server for a large
number of previously unknown users, without requiring
preexisting trust relationships between users
and the system.
Our prototype requires no modifications to either
servers or browsers, and makes use of graphical
Turing tests, web proxies, and client authentication
using the SSL/TLS protocol, all readily supported
by modern browsers. We use the WebSOS
prototype to conduct
a performance evaluation over the Internet using
PlanetLab,
a test bed for experimentation with network overlays.
We determine the end-to-end latency using both
a Chord-based
approach and our shortcut extension. Our evaluation
shows the latency increase by a
factor of 7 and 2 respectively,
confirming our simulation results.
A
Distributed Denial of Service Attack
The Target Server becomes unusable as
the attackers inject more a more traffic towards
the Target Server. The routers on the path to
the Target exhibit network congestion starting
with the ones that are closer to the Target.
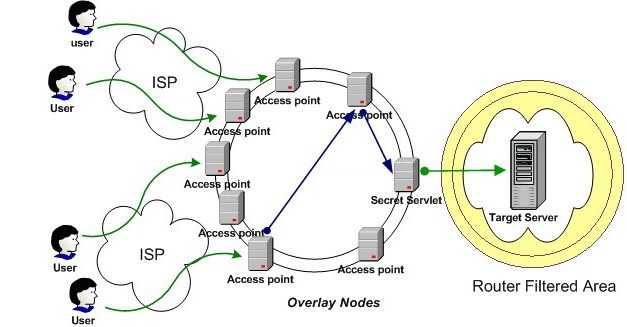
WebSOS
Architecture under DDoS attack
|
| WebSOS acts as a distributed firewall
eliminating communication pinch-points and thus
preventing the Target Server's Routers from being
congested. The user need to connect securely to
an Access Point and the overlay network route
him to the actual Target Server. The Target server
allows only the secret servlet (or a set of secret
servelts) to connect through the filtered Area.
The filtering is done using fields that a router
can filter fast (e.g. the IP address of the secret
servlet). The secret servlet's location can be
varied through time.
The disruption in the actual service depends
on the number of the secure overlay access points,
the resources and distribution of "zombies"
of the actual attacker. The addition of the Graphic
Turing Tests allows us to accept non-authenticated
traffic which is something that most web services
require. Additionally Graphic Turing tests separate
humans from automated attack scripts and allow
us more protection against naive automated attacks.
Finally GTTs provide the necessary time for the
overlay "heal" from the automated attacks.
They prevent traffic to penetrate the overlay
network and being routed to the Target server
thus making the actual Web service more resilient
to DDoS attacks. |
|
|
People
|
Angelos
Stavrou, PhD student, Computer Science Department,
Columbia University
Angelos
D. Keromytis, Professor, Computer Science
Department, Columbia University
Vishal Misra, Professor, Computer Science
Department, Columbia University
Dan Rubenstein,
Professor, Electrical Engineering Department,
Columbia University
Previous Collaborators:
Debbie
Cook, Ph.D. student, Computer Science Department,
Columbia University
William G. Morein, Masters student, Computer
Science Department, Columbia University
|
|
|
Publications and Presentations
|
Journal Publications:
"SOS: An Architecture for
Mitigating DDoS Attacks"
Angelos D. Keromytis, Vishal
Misra, and Dan Rubenstein. In IEEE Journal on Selected Areas in
Communications (JSAC), special issue on Recent Advances in Service
Overlay Networks, vol. 22, no. 1, pp. 176 - 188. January
2004.
Conference Proceedings:
" A Pay-per-Use DoS Protection Mechanism For The Web"
Angelos Stavrou, John Ioannidis, Angelos D. Keromytis, Vishal Misra, and Dan Rubenstein.
In Proceedings of the
Applied Cryptography and Network Security (ACNS) Conference. June 2004, Yellow Mountain, China. LNCS Volume 3089/2004, pp. 120-134, ISBN: 3-540-22217-0
"Using Graphic
Turing Tests to Counter Automated DDoS Attacks
Against Web Servers"
William G. Morein, Angelos Stavrou, Debra L. Cook,
Angelos D. Keromytis, Vishal Misra, and Dan Rubenstein.
In Proceedings of the 10th ACM International Conference
on Computer and Communications Security (CCS),
pp. 8 - 19. October 2003, Washington, DC.
"WebSOS:
Protecting Web Servers From DDoS Attacks"
Debra L. Cook, William G. Morein, Angelos D. Keromytis,
Vishal Misra, and Daniel Rubenstein. In Proceedings
of the 11th IEEE International Conference on Networks
(ICON), pp. 455 - 460. September/October 2003,
Sydney, Australia.
"Secure Overlay
Services"
Angelos D. Keromytis, Vishal Misra, and Dan Rubenstein.
In Proceedings of the ACM SIGCOMM Conference,
pp. 61 - 72. August 2002, Pittsburgh, PA.
WebSOS+GTT Presentation
for CCS 2003 |
|
|
WebSOS Code Releases
|
WebSOS ALPHA release:
Source Code JAVA and C modules [tar.gz]
[zip]
Installation instructions & Documentation[PDF]
[PS]
|
|
|