Software & System Assurance
|
Autonomic Software Patching
|
|
The network worm vaccine architecture is a system that is designed to automatically
patch and defend systems and networks under attack by worms or other network threats.
The ability of worms to spread at rates that effectively
preclude humandirected reaction has elevated
them to a firstclass security threat to distributed
systems. We present
the first reaction mechanism that seeks to automatically
patch vulnerable software. Our system employs
a collection of sensors that detect and capture
potential worm infection
vectors. We automatically test the effects of
these vectors on appropriatelyinstrumented sandboxed
instances of the targeted application, trying
to identify the exploited soft
ware weakness. Our heuristics allow us to automatically
generate patches that can protect against certain
classes of attack, and test the resistance of
the patched application against the infection
vector.
Further research on extending this architecture
to capture a wide range of known and unknown attacks
is underway. Currently, we're extending the architecture
with the ability to capture email worms by introducing
a host-based intrusion detection mechanism for
the instrumented application.
Students interested in participating in the project,
please refer to our student
project page. |
|
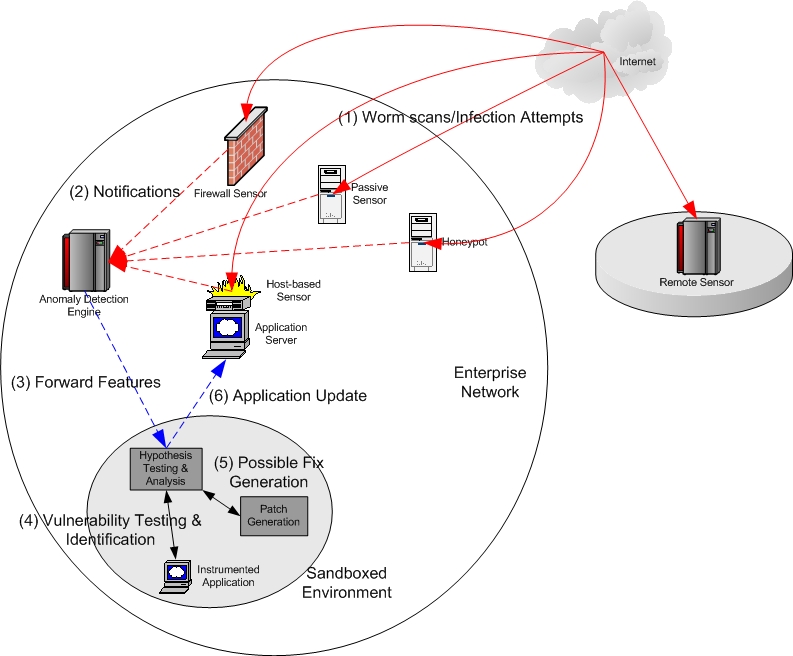
The Network Vaccine Architecture
|
|
Publications
|
- "A
Network Worm Vaccine Architecture"
- Stelios Sidiroglou and Angelos D. Keromytis. In Proceedings of
the IEEE International Workshops on Enabling Technologies: Infrastructure
for Collaborative Enterprises (WETICE), Workshop on Enterprise Security.
June 2003, Linz, Austria.
-
"Countering Network Worms Through Automatic Patch Generation"
- Stelios Sidiroglou and Angelos D. Keromytis. Columbia University technical report
CUCS-029-03. November 2003, New York, NY.
-
"An Email Worm Vaccine Architecture"
- Stelios Sidiroglou, John Ioannidis,
Angelos D. Keromytis, and Salvatore J. Stolfo. To appear in the Proceedings of
the 1st Information Security Practice and Experience Conference (ISPEC) April 2005, Singapore
-
"Building A Reactive Immune System for Software
Services"
- Stelios Sidiroglou, Michael E. Locasto, Stephen
W. Boyd, Angelos D. Keromytis. To appear in the
Proceedings of the USENIX Annual Technical
Conference. April 2005, Anaheim,CA
- "Hardware Support For Self-Healing Software
Services"
- Stelios Sidiroglou, Michael E. Locasto, and
Angelos D. Keromytis. In the Proceedings of the Workshop
on Architectural Support for Security and Anti-Virus (WASSA), held
in conjunction with the 11th International Conference on
Architectural Support for Programming Languages and Operating Systems
(ASPLOS-XI). October 2004, Boston, MA.
- "Countering Network Worms Through Automatic Patch
Generation"
- Stelios Sidiroglou and Angelos
D. Keromytis. To appear in IEEE Security & Privacy. 2005.
-
"A Dynamic Mechanism for Recovering from Buffer
Overflow Attacks"
- Stelios Sidiroglou, Giannis Giovanidis, and
Angelos D. Keromytis. To appear in the Proceedings of
the 8th Information Security Conference
(ISC). September 2005, Singapore. An older
version of this paper is available as
Columbia University Computer Science Department
Technical Report CUCS-031-04, September 2004.
(Acceptance rate: 14%)
- "Patch-on-Demand Saves
Even More Time?"
- Angelos D. Keromytis. In IEEE
Computer, vol. 37, no. 8, pp. 94 - 96. August
2004.
|
|
|
|
|
|